
Resilient Kill Chains Through Cyber Mission Thread Analysis
During my time with the Air Force Lifecycle Management Center, I provided systems engineering support to the Air Force Cyber Engineering Directorate at the Cyber Resiliency Office for Weapon Systems (AFLCMC EN-EZ CROWS) as a Deputy Program Manager.
CROWS is an Air Force unit that was stood up in late 2017 in an effort to analyze the cyber vulnerabilities of fielded and future major weapons systems and report findings back to Congress. Established under the Assistant Secretary of the Air Force for Acquisition, Technology & Logistics to ensure Air Force weapon systems can perform their missions in a cyber-contested environment and under adverse conditions, CROWS is focused on advancing the cyber resiliency of weapon systems to maintain mission effectiveness.

CROWS’s is the first major service to tackle cyber vulnerability of fielded weapon systems and address congressional committees.
Analyzing Air Force Combat Missions for determined state or non-state actor cyber adversary exploits, they partner with acquisition, operational and test communities to evaluate the fielded fleet and with Program Executive Offices to prototype mitigation solutions. CROWS also delivers cyber-focused intelligence, a common security environment, education & training, and invaluable cyber focus teams dedicated to guiding acquisition directorates on cyber-related topics.

In addition to being an excellent resource for providing the trade craft, tools & knowledge necessary to address modern cyber threats to Air Force weapons systems, CROWS developed the System Security Engineering Cyber Guidebook (see chart above), and is the first major service to tackle cyber vulnerability of fielded weapon systems and address congressional committees.
Bad Actors In Cyberspace
Malicious cyber activity has evolved from trivial defacements to sophisticated operations targeting national security and public trust. These include espionage, intellectual property theft, attacks on critical infrastructure, ransomware, and influence campaigns aimed at destabilizing democratic institutions. Offensive cyber tools, once restricted to elite state actors, are now accessible to a wider range of adversaries, including criminal syndicates and lesser-resourced nations, amplifying the threat landscape.
Autocratic states like China, Russia, Iran, and North Korea exploit advanced cyber capabilities to outfox adversaries and challenge U.S. interests and international norms. Among them, China poses the most comprehensive and strategic threat. The People’s Republic has expanded its cyber operations beyond theft to dominance in emerging technologies and digital governance. By exporting its model of digital authoritarianism, China seeks to reshape the global internet, undermining privacy and human rights worldwide while challenging U.S. influence in the digital age.

Cyber Intrusions That Shook Defense
2020 SolarWinds Hack: Attributed to Russia, this sophisticated supply chain attack compromised multiple U.S. government agencies, including the DoD, by inserting malicious code into SolarWinds’ Orion software updates. This breach allowed attackers to infiltrate and monitor networks undetected.
2024 Acuity Data Breach: In April 2024, the hacker group IntelBroker, in collaboration with Sanggiero, breached Acuity, a U.S. government contractor. They accessed confidential information related to the Five Eyes intelligence organization and the U.S. military, including communications and documents stored on a GitHub repository.
2024 Europol Data Breach: On May 10, 2024, IntelBroker announced the theft of 9,128 confidential records from Europol, including employee information, source code, and guideline documents. Europol confirmed the breach but stated that no operational data was stolen.
2023 Pentagon Document Leak: A 21-year-old Air National Guardsman from the U.S. was implicated in leaking highly classified DoD documents through an online Discord group. This breach led to a sweeping review of security protocols and access controls, highlighting vulnerabilities in the distribution of sensitive information.
2024 Logistics System Vulnerability: The DoD’s reliance on multiple, siloed logistics management systems introduces significant cybersecurity risks. These systems, used to track and manage military supply chains, transmit sensitive data over unsecured networks, creating opportunities for exploitation by adversaries.
2023 North Korean Ransomware Operations: Cyber actors associated with North Korea targeted critical U.S. infrastructure, demanding ransoms in cryptocurrency. While not directly tied to DoD systems, these campaigns exposed vulnerabilities in adjacent systems vital to defense operations.
2022 State-Sponsored Cloud Breach: A state-sponsored actor, reportedly linked to China, exploited cloud-based services used by the DoD to access sensitive but unclassified information. The breach underscored the need for robust zero-trust architecture to secure multi-tenant environments.
2022 Russian Social Engineering Campaign: Russian operatives leveraged phishing schemes and social engineering to target DoD contractors, aiming to extract details about military technologies. This attack exposed weaknesses in the human element of cybersecurity and contractor oversight.
For decades Russia has leveraged its cyber capabilities to destabilize neighboring nations and meddle in the domestic politics of democracies worldwide. As a persistent cyber threat, Russia continues to advance its skills in espionage, cyberattacks, disinformation, and influence operations. These efforts aim to intimidate sovereign states, shield transnational criminal networks, undermine U.S. alliances, and challenge the rules-based international order. To address these challenges, the Air Force developed the Cyber Campaign Plan.

For a comprehensive deep dive into the rapidly evolving arena of cyber deception operations, please see:
Charismatic Code: The Art and Science of Cyber Deception
Air Force Cyber Campaign Plan
The Air Force Cyber Campaign Plan’s (CCP) overall mission has two primary goals: “Bake in” cyber resiliency into new weapon systems and mitigate “critical” vulnerabilities in already fielded weapon systems. The group established the Cyber Resiliency Steering Group (CRSG) comprised of eight (8) voting members (SAF/AQR, LCMC, SMC, NWC, AFTC, Intel, SAF/CISO, & 24AF/CV) along with a governance body to guide the AF Cyber Campaign Plan (CCP).
| Provide mission assurance through CMTA across core AF functions | |
| Enable cyber resiliency engineering and bake into all AF programs | |
| Recruit, hire & train a cyber savvy workforce | |
| Enhance weapon system adaptability and agility | |
| Develop a common security environment | |
| Assess legacy systems and mitigate risks | |
| Improve intelligence for cybersecurity |
The Air Force also established a dedicated unit to manage execution under the Cyber Resiliency Office for Weapon Systems (CROWS) with a focus on executing seven (7) lines of action (see table above). The campaign will also manage and execute the NDAA 1647 Weapon System Assessments and Mitigations in coordination with acquisition, test and evaluation communities in both the Air Force and the Space Force.
How are vulnerabilities of aircraft and weapon systems different from defending business networks and computer information systems?
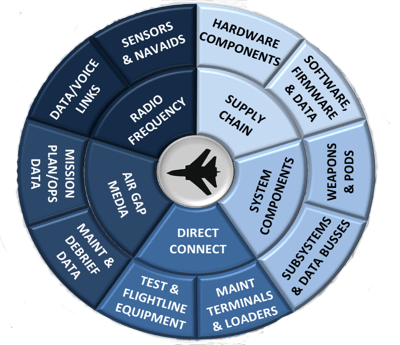
The Air Force defines cyber resilience in military systems as the ability of weapons systems to maintain mission effective capability under adversary offensive cyber operations and to manage the risk of adversary cyber intelligence exploitation. Weapon systems differ greatly from networks, computer information systems and business IT systems in ways that matter for implementing cyber resiliency. In most business situations, networks and information systems software and hardware design is usually commercial off the shelf (COTS), based on common architectures and standardized interfaces such as Windows and Linux. This is usually not the case in military systems where software and hardware design is often under government control, spans many diverse architectures, and involves customized interfaces.
Resilient Business Services (a.k.a. missions)
With five core missions and 42 capabilities, the Air Force prosecutes its vision of global reach, global power and global vigilance by providing business services to Air Force customers. These business services are organized in an interdependent taxonomy of combat support and include mission areas such as in-air refueling, rapid global mobility, suppression of enemy air defenses (SEAD), close air support (CAS), space situation awareness, and thirty seven (37) others (see video below).
Cyber Mission Thread Analysis (CMTA)
In PW Singers Cybersecurity and Cyber War, resiliency is defined as “understanding how the different pieces fit together and then how they can be kept together or brought back together when under attack”
CMTA is an enterprise level approach to people, process and technology that uses a common, repeatable mission level cyber analytic risk assessment methodology to identify and evaluate ways missions can be impacted by a determined cyber adversary. The approach is to identify and prioritize candidate mission threads, apply a common repeatable framework for CMTA, and prioritize and implement recommendations where appropriate and feasible.

Outputs produced include a prioritized list of cyber vulnerabilities across all mission areas that is briefed to new programs so they can build in resiliency, a prioritized list of cyber vulnerabilities across all mission areas that legacy programs need to fix and a prioritized list of critical capabilities the science and technology community must address.
A functional level analysis is accomplished through functional decomposition and functional flow diagrams. The functional decomposition is continued to the level of supporting systems, using methods such as those in Fault Tree Analysis (FTA). Then a ranking and triage process ensues leading to a system level analysis with functional decomposition, functional flow, and information flow diagrams. This helps determine which systems support the elements that remain after functional-level triage. Another ranking and triage process occurs using markers including cyber separability, cyber distance, dependencies and timing. In cyber separability two systems are cyber separable from one another if no single cyber vector of attack could simultaneously degrade the functionality of both systems. This ultimately leads to insight into the highest level of cybersecurity risks across both platforms and missions, enhanced with the addition of current intelligence reporting.
Conclusion:

Zero day exploits of weapon systems add to mission risk with the problem typically spanning programming, acquisition, operations and sustainment. A mission and platforms centric focus is necessary to ensure systems operate correctly and securely as part of a larger system of systems. Uncoordinated mitigation efforts may lead to costly inefficiencies, and risk accepted by one system is inherited across the enterprise.
Mission oriented analysis can identify risks and potential mitigations not apparent at the platform or system level, as mitigations often need to cross Program Executive Offices (PEO’s) for integration to occur. Through the prosecution of the Air Force Cyber Campaign Plan, the CROWS will ensure cyber resiliency is baked into new weapon systems and delivers intelligence and tools to mitigate critical vulnerabilities in already fielded weapon systems.
Acknowledgements and Image Credits:
{1} National Defense Authorization Act FY 2020 https://congress.gov/bill/116th-congress/senate-bill/1790
{2} United States Air Force, officially released photograph, 2019
{3} United States Air Force, Air Force Institute of Technology, Cyber Resiliency for Aircraft and Other Weapon Systems, AFMC 2015-0084 , Distribution A; https://youtu.be/hRzx6SLmU28
{4} Singer, P.W., Cybersecurity and Cyber War, 2013 Oxford University Press
{5} LOA1 Cyber Mission Thread Analysis, 2017 AFLCMC EN -EZ CROWS Distribution A
{6} Cyber Intrusions that Shook Defense. Image Credit: Fancy Bear
{7} Cyber Resiliency Office for Weapon Systems. Image Credit USAF CROWS


















































Pingback: Charismatic Code: The Art and Science of Cyber Deception |
Pingback: Data Center Warfare | The Race to Data Supremacy |
Pingback: Cosmic Conflict: 17 Stages to Space Superiority
Pingback: China in New England |