
In a rapidly evolving and ever accelerating world, where technology seems to advance at the speed of light, one field has seen remarkable progress – the development of targeting technologies and surveillance sensors using artificial intelligence and the release of numerous large language models and generative AI tools. New systems equipped with artificial intelligence are transforming the way military and law enforcement agencies operate, providing them with unprecedented capabilities for intelligence gathering, threat detection, and more.
The Rise of AI in Surveillance
In this report, we will unpack how artificial intelligence has revolutionized the surveillance game, turning what was once slow detective work into near-instant precision targeting. From the U.S. strike that killed Iranian Quds Force commander Qasem Soleimani to the recent takedowns of top drug cartel leaders, AI-powered surveillance tools have moved from theory to real-world impact. These systems can digest oceans of data—video feeds, sensor networks, even social media chatter—and zero in on high-value targets in ways that human operators simply cannot match.
What AI brings to the table is speed, scale, and foresight. Modern surveillance networks don’t just record; they anticipate. AI systems can:
- Process massive datasets in real time from cameras, drones, sensors, and online sources.
- Detect anomalies and patterns that point to criminal or terrorist activity.
- Identify and track suspects with facial recognition or object detection.
- Predict threats by analyzing historical behavior and movement patterns.
- Alert authorities instantly when someone enters a restricted zone.
- Cut through noise by filtering irrelevant footage, storing only what matters.
- Deploy AI-equipped drones to patrol vast, remote, or dangerous areas autonomously.
In practical terms, this means law enforcement can locate a fugitive in a crowd, prevent a bombing before it happens, or intercept a cartel shipment before it hits the streets. Yet these capabilities come with a warning label: the same technology that can stop a terrorist can also turn entire cities into surveillance states.
““The real fears that I have are not the ones that most people talk about AI — I talk about extreme risk. Think about North Korea, or Iran, or even Russia, who have some evil goal. This technology is fast enough for them to adopt that they could misuse it and do real harm.”
Eric Schmidt, former CEO of Google
“I always worry about the Osama bin Laden scenario, where you have some truly evil person who takes over some aspect of our modern life and uses it to harm innocent people.””
Date: February 13, 2025
Location: Paris, France — speaking on BBC Radio 4’s Today program following the AI Action Summit
Smart Cameras and Facial Recognition
Artificial intelligence-driven smart cameras are rapidly reshaping how law enforcement and security agencies operate. By combining high-definition imaging with real-time AI analysis, these systems can automatically identify individuals, detect suspicious behaviors, and cross-reference faces against massive databases in seconds. Facial recognition in particular has become a powerful capability—used to locate missing persons, identify suspects in crowded environments, and strengthen border security. In some cities, police have begun integrating smart cameras into broader surveillance networks, allowing them to track persons of interest across multiple locations in near real-time. The efficiency and speed of these tools have the potential to dramatically enhance public safety by providing authorities with faster, more reliable information than ever before.
Yet the rise of facial recognition also carries profound ethical and privacy implications. Critics warn that widespread deployment risks creating a culture of constant surveillance, where individuals’ movements are monitored without consent. Studies have shown that algorithms can sometimes produce biased outcomes, misidentifying women and minorities at higher rates—a flaw with potentially serious consequences when applied in law enforcement. Beyond technical accuracy, the bigger concern is governance: who controls the data, how it is used, and what safeguards exist to prevent abuse. As governments and agencies expand their reliance on smart cameras, society faces a difficult balance between leveraging the benefits of AI-enabled identification and preserving fundamental rights to privacy and freedom of movement.
LiDAR Technology: A Game Changer
One of the most significant breakthroughs in surveillance technology is LiDAR (Light Detection and Ranging). LiDAR sensors use laser pulses to create high-resolution 3D maps of the environment. This technology has found crucial applications in autonomous vehicles, but it’s also revolutionizing the way surveillance is conducted. LiDAR’s ability to create detailed 3D maps enables precise targeting. Military drones and surveillance systems equipped with LiDAR can identify targets with incredible accuracy, reducing collateral damage and increasing mission success rates.
ViDAR (Visual Detection and Ranging) Powered by AI

Sentient Vison is a leading developer of Computer Vision and Artificial Intelligence software solutions for defense and law enforcement. They have developed ViDAR (Visual Detection and Ranging), the world’s first Optical Radar, a maritime wide area optical search system proven to operate up to Sea State 6. ViDAR autonomously finds objects on the surface of the ocean over vastly greater areas than traditional search methods. ViDAR is able to detect objects that are very small – much beyond the capability of the human eye – to dramatically extend the coverage of the aircraft in a broad range of search missions including search and rescue, illegal fishing, counter narcotics and maritime security.
A Defense & Security Data Fabric Powered by AI
In order to meet the demands of the rapidly evolving future operating environment, US and allied defense leadership need to develop courses of action for progressively complex dilemmas that are paramount to plan for conflict, avoid surprise by unforeseen crisis, and fully grasp the implications of shifting global challenges. The information and cyber domains have become particularly challenging, serving as a live battle lab for adversaries testing techniques and tactics, state sponsored operations, attacks on smart power grids, autonomous vehicles, IOT, and the growing threats to deployed forces and civilian populations from disinformation weaponization.
Modeling and simulation of scenarios for how events are likely to unfold is invaluable insight that can significantly improve command and control decisions. However, many tools in this field are siloed and thus frustrating analysts’ efforts. The challenges are: difficulty accessing data for modeling, inability to provisioning the most appropriate tools and lack of interoperability to integrate them in the moment.
The Defense Simulation Analytical Service (DSaS), powered by AI & Red Hat OpenShift, is a defense data fabric for CIA and Air Force Intelligence officers, and offers commanders and analysts a scalable platform ecosystem that allows an operation center to leverage data, visualizations, simulation capabilities, and decision support that can help determine the best course of action at the speed of relevance with holistic cross-domain consideration.
IBM’s DSaS is an open source software platform built on Red Hat OpenShift that presents capabilities from an ecosystem of providers – both industry and defense – to analysts in a marketplace that can be assembled to support a wide range of scenarios. OpenShift allows those capabilities to run on any cloud infrastructure provider, on premises and out to the edge. This offers scale and global reach to support operations in contentious scenarios wherever they are in the world.

In this Ukraine Scenario from The American Enterprise Institute for example:
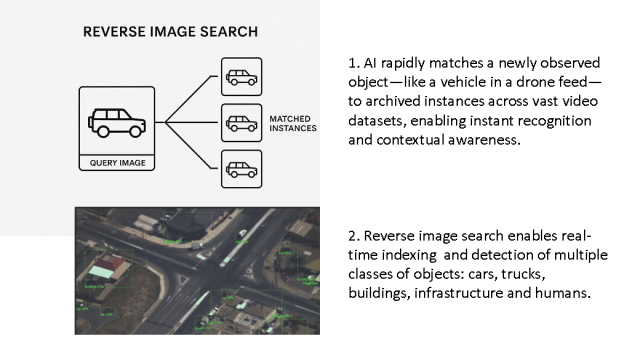
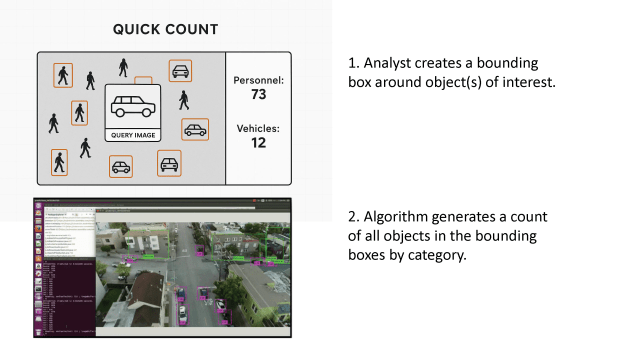
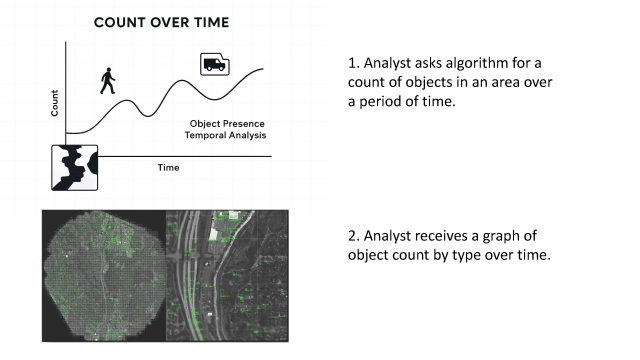
1. An analyst can choose from a wide range of visuals from city and local monitoring, city aerial view feed, roadway and traffic cameras, drones with high overhead tactical views, air traffic and commercial environmental monitoring.
2. Is able to review emerging media (social & TV news) related to Russia’s recent air/land/sea/space activity around Ukraine.
3. Obtains live monitoring via real time and recent satellite and social images.
4. Receives automated visual views with feeds and analytics that are automatically filtered based on activity and relevance.
Defense & Security enterprise data readiness for the era of generative AI
Fragmented data stacks, productivity pressures and the lack of data preparedness for generative AI are driving enterprises to evaluate new data strategies. As we have seen in this case study, data fabric is designed to bring the power of generative AI to streamline the integration, curation, governance and delivery of high-quality data for analytics and artificial intelligence (AI).
Data fabric introduces new data intelligence and integration tools to prepare data for generative AI, helping to ensure readiness for both structured and unstructured data in AI initiatives. By streamlining data preparation and integration, defense, security and law enforcement organizations can unlock productivity for their data analysis teams and drive business innovation that creates better mission outcomes.
AI and Machine Vision In The Fight
In today’s fast-paced operational environments, artificial intelligence isn’t just a tool—it’s a force multiplier. From battlefield awareness to strategic tracking, AI systems like those developed for air force intelligence operators, CIA station chiefs, and other Federal enterprise security personnel are transforming how decisions are informed, automated and made.
Below are five powerful examples of “AI in the Fight,” each showing how machine learning and computer vision augments human capabilities with precision and insight at the speed of war.
The New Eyes of Surveillance
For centuries, humans have tried to see further, clearer, and sooner than their rivals. From the watchtowers of ancient cities to Cold War satellites, surveillance has always been about extending the human eye. Today, that eye is evolving faster than ever. Artificial intelligence, quantum physics, and a new generation of sensors are converging to create a surveillance ecosystem.
Quantum Radar: Piercing the Veil of Stealth
One of the most ambitious frontiers is quantum radar, a concept first theorized in the mid-2000s. Unlike traditional radar, which bounces radio waves off objects, quantum radar uses pairs of entangled photons. Even if one photon is scattered in noise, its twin still carries the imprint of the target. In theory, this could allow radars to spot aircraft designed to evade conventional detection.
Lockheed Martin patented early concepts, while Chinese researchers have claimed recent breakthroughs in programmable quantum radar. The technology remains experimental, but if proven, it could render stealth aircraft far less invisible than their designers intended.
Synthetic Aperture Radar: Old Tech, New Power
Not all surveillance breakthroughs are futuristic. Some, like synthetic aperture radar (SAR), date back to the 1950s. SAR works by stitching together radar signals collected as an aircraft or satellite moves, producing sharp, photo-like images of terrain, even through clouds or darkness.
First deployed on Cold War spy satellites, SAR remains indispensable today. NASA’s Earth-monitoring satellites use it to map forests, while the U.S. military relies on it to track movements across battlefields. Far from obsolete, SAR shows how legacy technologies can gain new relevance when fused with modern AI analytics.
The Human Heart as an Identifier
Biometrics once meant fingerprints or facial recognition. Now, even the heartbeat is a unique signature. In 2019, the U.S. Department of Defense revealed “Jetson,” a laser-based system that can detect the subtle vibrations of a person’s chest from up to 200 meters away. Each heartbeat pattern—sometimes called a “heartprint”—is distinct, offering a new form of remote identification.
While not yet widespread, the idea of using heart rhythms as an ID system illustrates how the human body itself has become the ultimate password in the surveillance era.
Detecting What Lies Beneath
Surveillance isn’t just about the sky—it’s also about the ground. Governments have long feared tunneling as a way to bypass borders or infiltrate secure sites. In 2011, Raytheon engineers patented a seismic-based subsurface detection system capable of distinguishing between footsteps above ground and digging activity below it.
By listening to vibrations deep underground, such sensors can spot intruders long before they surface. In a future of hardened borders and subterranean warfare, underground surveillance may prove as important as aerial monitoring.
Seeing Through Wi-Fi
Surveillance has also begun to co-opt the signals all around us. In 2018, researchers demonstrated how ordinary Wi-Fi signals can be used to detect human presence and even monitor breathing patterns—without cameras or specialized gear.
This technique leverages the way wireless signals bounce and scatter around moving bodies. In practice, it could transform every Wi-Fi router into a potential motion detector. While still mostly confined to research labs, the implications for privacy are immense.
Walking as a Fingerprint
Another emerging biometric is gait recognition—the science of identifying individuals by the way they walk. Embedded floor sensors or advanced cameras can analyze stride length, weight distribution, and cadence. Because gait is difficult to consciously disguise, it provides a persistent form of recognition even when faces are hidden.
Universities in the U.K. and China have led much of the early research, but the technology is slowly creeping into commercial and security systems. In the future, simply walking through a space could be enough to trigger an identity check.
Tracking the Microbiome
Perhaps the most unusual surveillance innovation lies in the human microbiome. Research has shown that each person emits a unique cloud of microbial life—bacteria and microscopic particles—that lingers in the air. By sampling and analyzing this microbial signature, scientists suggest it may be possible to identify individuals or reconstruct their movements through a space.
Still in its infancy, microbiome surveillance represents the merging of biology and intelligence collection. What once seemed like science fiction—the idea that even the microbes you shed could betray your identity—is moving toward possibility.
The Smell of Identity
Closely related is the field of odor biometrics. Every person has a distinctive chemical scent, shaped by genetics, diet, and health. Researchers are developing sensors capable of capturing and cataloging these invisible “odor signatures.”
Though practical deployment remains limited, scent-based recognition could one day join fingerprints, faces, and voices as part of the biometric toolkit. The very air around us may no longer be neutral—it may carry identifiers as unique as DNA.
Quantum Sensors: Mapping the Invisible
Beyond individual identities, quantum technology is also redefining how we sense the physical world. Quantum magnetometers can detect minute disturbances in magnetic fields, potentially exposing hidden submarines or underground structures. Quantum gravimeters measure slight shifts in gravity to map subterranean tunnels or detect vehicles through walls.
Developed through major national research programs in the U.K., U.S., and EU, these sensors are edging from laboratory to field deployment. Their promise is nothing less than to make the invisible visible.
Networks That Cannot Be Intercepted
Finally, the surveillance ecosystem is being bound together by quantum-secure networks. By integrating quantum key distribution (QKD) with sensor arrays, data can be transmitted securely between satellites, drones, and ground stations—immune to interception by even the most advanced adversaries.
DARPA, NATO, and the European Quantum Flagship are all exploring these systems, which could underpin the next generation of military and intelligence architectures. In a world where data is as valuable as detection, securing the flow of information is as vital as gathering it.
The New Landscape
Taken together, these ten technologies signal a transformation. Surveillance is no longer limited to cameras and satellites—it extends into quantum states, biological signatures, and the invisible forces of magnetism and gravity.
Each advance raises profound questions: What happens when the human body itself is the ultimate tracking beacon? How should societies balance safety against privacy when even a heartbeat or a microbe can reveal identity?
What is clear is that the future of surveillance will not be a single technology, but a layered ecosystem—quantum-enhanced, AI-driven, and biologically attuned. In that future, the line between security and intrusion will be defined less by what can be seen, and more by what we choose to allow ourselves to see.
Law enforcement and intelligence services in the United States possess technology to remotely activate the microphones in cell phones in order to listen to conversations that take place nearby the person who holds the phone.


SORM (Russia) A system used by the Federal Security Service of the Russian Federation to monitor internet and telephone communications.
Golden Shield (China): Also known as the “Great Firewall of China”, it is a censorship and surveillance project operated by the Ministry of Public Security (MPS)


PRISM (USA): A clandestine national security electronic surveillance program operated by the National Security Agency (NSA) that can monitor US and International Corporations.
Central Monitoring System (CMS) (India): A data collection system similar to the NSA’s PRISM program. It enables the Government of India to listen to phone conversations, intercept e-mails and text messages, monitor posts on social networking service and track searches on Google.


Project 6 (Germany): A global surveillance project jointly operated by the German intelligence agencies Bundesnachrichtendienst (BND) and Bundesamt fur Verfassungsschutz (BfV) in close cooperation with the U.S. Central Intelligence Agency (CIA).
Royal Concierge (United Kingdom): Sends daily alerts to GCHQ whenever a booking is made from a “.gov.” second-level domain at select hotels worldwide.


X-Keyscore (USA): A system used for searching and analyzing internet data in real time.
INDECT (European Union): Research project funded by the European Union to develop surveillance methods (e.g. processing of CCTV camera data streams) for the monitoring of abnormal behaviors in an urban environment.

Conclusion
Artificial intelligence is no longer a supporting tool in surveillance and targeting—it is the operational backbone. From precision strikes like the removal of Iran’s Quds Force commander to the dismantling of major drug cartel leaders, AI-enabled systems are proving their value in delivering decisive, real-world outcomes. These technologies are accelerating decision cycles, fusing intelligence from multiple domains, and ensuring that agencies can act faster and with greater accuracy than ever before. Yet, with this capability comes an urgent responsibility: balancing speed and effectiveness with transparency, oversight, and the protection of civil liberties.
As AI expands across the battlespace and into law enforcement operations, its role will only deepen. For policymakers, technologists, and security leaders, the central challenge is to maximize the advantages of automation while avoiding the risks of overreach or misuse. Done right, AI-powered surveillance and targeting can transform security strategy, shaping a future where intelligence is not just collected—but operationalized at scale. In short, it promises to better inform how to deliver the right war-winning capabilities, when and where needed.
Additional Information
About PWK International Advisers
PWK International provides national security consulting and advisory services to clients including Hedge Funds, Financial Analysts, Investment Bankers, Entrepreneurs, Law Firms, Non-profits, Private Corporations, Technology Startups, Foreign Governments, Embassies & Defense Attaché’s, Humanitarian Aid organizations and more.
From cognitive partnerships, cyber security, data visualization and mission systems engineering, we bring insights from our direct experience with the U.S. Government and recommend bold plans that take calculated risks to deliver winning strategies in the national security and intelligence sector. PWK International – Your Mission, Assured.

























































Pingback: Unmanned Arsenal: Emerging Trends in The Business of Drones |
Pingback: Anduril’s Edge: A New Era of Defense Innovation |
Pingback: Smart Borders: How Technology is Tracking You |
Pingback: Algorithmically Boosted Chaos |