
From Leonardo Da Vinci to Renaissance Technologies
In the annals of history, few figures command as much admiration for their ingenuity and foresight as Leonardo da Vinci. Renowned for his masterpieces of art and groundbreaking engineering sketches, da Vinci was also a man keenly aware of the risks posed by intellectual theft and industrial espionage. Many of his most advanced ideas—designs for flying machines, weapons of war, and architectural innovations—were meticulously recorded in notebooks written in Latin, often backwards. This technique, a form of mirror writing, was likely intended not only to shield his work from prying eyes but also to ensure that only the most dedicated and knowledgeable individuals could decipher his visionary ideas.

Leonardo’s cautious approach to sharing his intellectual property highlights a recurring theme throughout history: the allure and danger of secrets. During the Renaissance, a period synonymous with innovation and discovery, industrial espionage was already taking root. Rival city-states in Italy frequently sought to steal technological and artistic advancements from one another, employing spies to infiltrate workshops and acquire trade secrets. In this context, da Vinci’s deliberate obfuscation of his work appears as a prescient response to the risks of intellectual property theft—an issue as pressing in his time as it is today.
Fast forward to the 21st century, and the stakes of protecting innovation have escalated dramatically. The tools of espionage have evolved from whispered conversations in candlelit workshops to sophisticated cyber intrusions orchestrated by state-sponsored actors and corporate competitors. One of the most intriguing modern parallels to Renaissance ingenuity is the hedge fund Renaissance Technologies. This highly secretive firm, known for its groundbreaking application of quantitative algorithms and artificial intelligence in financial markets, operates in an environment where the value of intellectual property cannot be overstated. Like da Vinci’s notebooks, Renaissance Technologies’ proprietary models and data-driven strategies are closely guarded, exemplifying how the art of concealing secrets has adapted to the digital age.

The enduring battle to protect innovation—whether in the form of artistic sketches, engineering blueprints, or proprietary algorithms—provides a compelling lens through which to examine the modern landscape of intellectual property theft. This report aims to explore how the challenges and methods of safeguarding innovation have evolved from da Vinci’s time to the present, with a focus on the policy and legal frameworks that underpin maintaining industrial secrets and game changing trade craft.
Historical Foundations of IP Protection: From Da Vinci to Today
The challenges faced by Leonardo da Vinci in safeguarding his innovations echo through the centuries, underscoring the timeless value of intellectual property protection. During the Renaissance, trade secrets were often guarded through rudimentary but effective means—encrypted manuscripts, trusted apprentices, and even misinformation to mislead potential thieves. Rivalries among city-states like Florence, Venice, and Milan created an environment where espionage flourished, driven by the desire to outmaneuver competitors in trade, art, and warfare.
One illustrative example comes from Venice, a maritime superpower that guarded the secrets of its shipbuilding industry with an iron fist. The Arsenal of Venice, a sprawling complex of shipyards and armories, was the epicenter of naval innovation. Workers and engineers were sworn to secrecy, and penalties for revealing trade secrets were severe. This culture of secrecy ensured Venice’s dominance in naval warfare for centuries, demonstrating the critical role of intellectual property in maintaining a competitive edge.
Stolen Naval Architecture - Renaissance to Today
China is widely reported to have reverse-engineered the design of the U.S. Navy’s Sea Hunter, an autonomous unmanned surface vessel (USV) developed for anti-submarine warfare and surveillance. Reports suggest that China’s vessel, resembling the Sea Hunter’s sleek trimaran design, incorporates similar stealth and autonomy features. This case highlights the ongoing challenge of safeguarding cutting-edge military technologies from foreign espionage and replication, with potential implications for maritime security and maintaining technological superiority in the anti access area denial (A2AD) great power contest in the Indo-Pacific.
As time progressed, the need for more formalized protections became evident. The first recorded patent laws emerged in Venice in 1474, providing inventors with exclusive rights to their creations for a limited time. This landmark development not only incentivized innovation but also laid the groundwork for modern intellectual property frameworks.
By the Industrial Revolution, the stakes had risen dramatically. Advances in machinery, chemistry, and engineering created a goldmine of intellectual property ripe for exploitation. Industrial espionage became a global phenomenon, with nations and corporations dispatching spies to infiltrate factories and laboratories. One famous case involved Francis Cabot Lowell, an American businessman who memorized the designs of British textile machines during a trip to England, ultimately revolutionizing the U.S. textile industry upon his return.
Today, the challenges of protecting intellectual property have reached unprecedented levels. Unlike the localized rivalries of the Renaissance or the industrial sabotage of the 19th century, modern economic espionage is a transnational threat. The rise of digital technologies has enabled actors to steal trade secrets with unparalleled speed and scale, often leaving victims with little recourse. From cyber intrusions to insider threats, the methods may have changed, but the motivations remain the same: to gain a competitive advantage by any means necessary.

Modern Economic Espionage: Mechanisms and Tactics
The landscape of economic espionage today is characterized by its sophistication and global reach. The integration of technology into every facet of business and government operations has opened new avenues for stealing trade secrets, often blurring the lines between legitimate competition and outright theft.
Cyber Intrusions: The Digital Frontier
One of the most prevalent methods of modern economic espionage is cyber intrusion. Hackers, often state-sponsored or backed by organized crime groups, infiltrate networks to exfiltrate sensitive data. Techniques such as phishing, malware, and zero-day exploits are common tools in their arsenal. For example, the 2014 hack of a major U.S. semiconductor company revealed how adversaries target key industries to gain a technological edge.
Insider Threats: Trust Betrayed
While cyberattacks dominate headlines, insider threats remain a significant challenge. Employees with access to critical information may be coerced, bribed, or even ideologically motivated to share secrets with competitors or foreign governments. There are numerous cases where insiders played pivotal roles in facilitating economic espionage, emphasizing the importance of robust vetting and monitoring processes.
Supply Chain Vulnerabilities
Another key vector for economic espionage is the supply chain. Adversaries exploit weaknesses in the production and distribution networks of high-tech industries to introduce compromised components or gain access to sensitive designs. This approach not only threatens intellectual property but also poses risks to national security.
Legal and Policy Loopholes
Economic espionage is often facilitated by gaps in international legal frameworks. Differing standards for intellectual property protection and enforcement create opportunities for bad actors to operate with impunity. For instance, some nations fail to recognize trade secrets as a protected category, allowing stolen information to be commercialized without repercussions.
Economic and Strategic Implications
The consequences of economic espionage extend far beyond the immediate victims. Stolen intellectual property can undermine the competitiveness of entire industries, lead to job losses, and erode public trust. Moreover, when state actors are involved, the stolen technologies often bolster military capabilities, shifting the global balance of power.
Addressing these challenges requires a multifaceted approach, combining robust cybersecurity measures, international cooperation, and comprehensive policy reforms. In the next chapter, we will explore the specific strategies and best practices that organizations and governments can adopt to mitigate the risks of economic espionage.

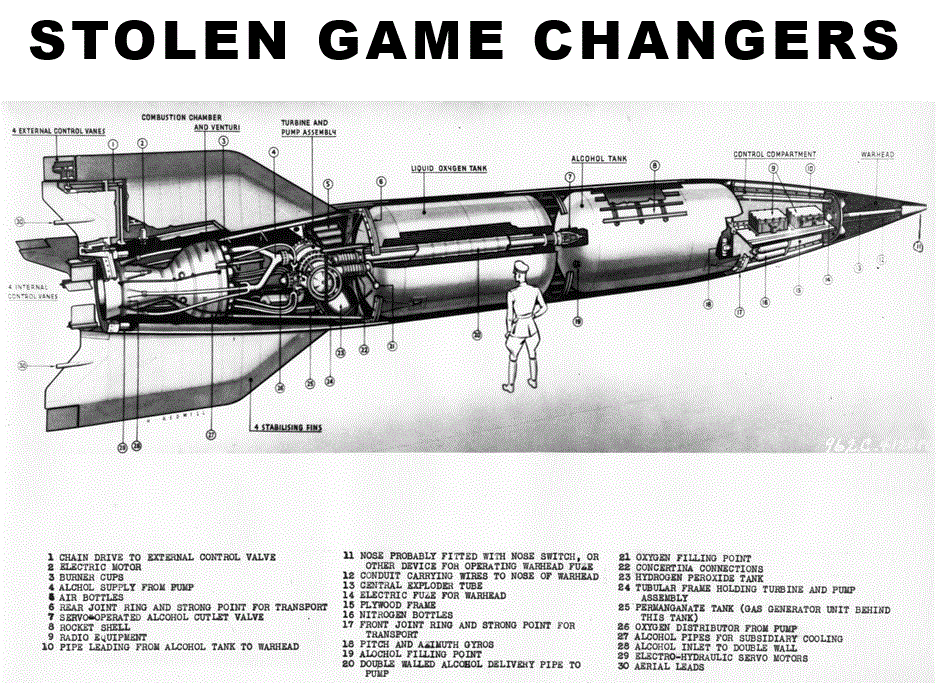
1. The Nazi V-2 Rocket Program
At the close of World War II, Nazi Germany developed the V-2 rocket, the world’s first long-range guided ballistic missile, and kept it secret at an underground R&D facility at Peenemunde. After the war, the U.S. scrambled to capture German scientists and V-2 designs, and send them to Alamogordo New Mexico, which significantly advanced the missile and space programs and accelerated the global arms race and space exploration.
2. DuPont’s Titanium Dioxide Theft
In the early 2000s, trade secrets about the production of titanium dioxide, a critical pigment, were stolen from DuPont and passed to Chinese entities. This insider-enabled espionage caused significant financial losses and underscored the global stakes in industrial innovation. The case remains a benchmark example of how economic espionage can destabilize competitive advantages.
3. Operation Aurora
In 2009, a cyberattack known as Operation Aurora targeted prominent companies like Google and Northrop Grumman. The attackers exploited software vulnerabilities to access sensitive intellectual property, allegedly under the direction of Chinese state actors. This incident demonstrated the increasing sophistication of cyber espionage and its implications for corporate and national security.
4. Boeing Industrial Espionage Case
Two Boeing engineers were convicted in the 1990s for stealing trade secrets related to rocket and space technologies. Their intent to share the information with competitors posed risks to national security and Boeing’s competitive edge. This case highlighted the vulnerability of critical industries to insider threats.
5. The Wright Brothers’ Patent Battle
In the early 1900s, the Wright brothers faced relentless attempts to replicate or steal their patented designs for powered flight. Rivals and governments sought to bypass their intellectual property, believing it crucial to military and commercial aviation. This case established the importance of robust intellectual property protections in groundbreaking innovation.
6. The Soviet Atomic Bomb Program
During the Cold War, Soviet agents infiltrated the Manhattan Project, stealing key secrets to develop their own atomic bomb. This intelligence coup accelerated the USSR’s nuclear capabilities, fundamentally altering the global balance of power. It remains one of history’s most consequential acts of scientific espionage.
7. The Concorde Supersonic Jet Espionage
The 1960s development of the Concorde, the first supersonic passenger jet, was marred by espionage as the Soviet Union stole key technical data. The stolen information helped them create the Tupolev Tu-144, a competing supersonic airliner. While the Tu-144 was less successful, the espionage underscored the stakes in high-tech aviation innovation.
8. Cisco and Huawei Router Espionage
In the early 2000s, Huawei, a Chinese telecommunications giant, was accused of stealing router technology from Cisco Systems. By reverse-engineering and copying designs, Huawei gained a competitive advantage in the global networking equipment market. The case became a flashpoint in debates over intellectual property theft in the tech industry.
9. U.S. Supercomputing Secrets
Throughout the 1990s and 2000s, U.S. supercomputing advancements were targeted by foreign operatives seeking to advance their own capabilities. Espionage efforts focused on hardware designs and software algorithms critical for military and scientific purposes. These thefts underscored the strategic value of computing power in defense and innovation.
10. Toshiba and the Soviet Propeller Case
In the 1980s, Toshiba illegally sold advanced milling machines to the Soviet Union, enabling quieter submarine propellers. This breach of Western export controls jeopardized NATO’s ability to track Soviet submarines during the Cold War. It highlighted the intersection of technology transfer and geopolitical competition.

Strategies for Combating Economic Espionage
A recent Congressional Research Service (CRS) report provides a comprehensive analysis of economic espionage and trade secret theft, shedding light on the actors, methods, and implications of this pervasive issue. Its findings reveal the scale and complexity of intellectual property theft in the modern era.
Key Actors in Economic Espionage
- Nation-States: Countries with strategic interests often engage in economic espionage to bolster their industries and military capabilities. China, Russia, and Iran are frequently cited as major players, leveraging state-sponsored cyber units and intelligence agencies to target foreign companies.
- Corporations: Rival firms, especially in high-tech sectors, sometimes resort to espionage to gain a competitive edge. This includes hiring third-party hackers or recruiting insiders to steal proprietary information.
- Empowered Individuals: Disgruntled employees, opportunistic insiders, or contractors may engage in theft for personal gain, ideological reasons, or under coercion.
The fight against economic espionage demands a comprehensive strategy that combines technological, legal, and organizational measures. Governments, corporations, and international bodies must work in concert to create an environment where intellectual property is rigorously protected and theft is deterred.
Technological Defenses: Strengthening Cybersecurity
Robust cybersecurity measures are the first line of defense against economic espionage. Organizations must invest in advanced threat detection systems, encrypted communication channels, and regular vulnerability assessments. Key recommendations emphasize the importance of adopting a proactive approach, such as implementing intrusion detection systems (IDS) and endpoint detection and response (EDR) technologies.
Training employees to recognize phishing attempts and other common attack vectors is equally critical. Human error remains a significant vulnerability, and fostering a culture of cybersecurity awareness can significantly reduce risks.



International Cooperation: Harmonizing Legal Frameworks
Economic espionage often exploits the gaps between differing national laws. International cooperation is essential to address these discrepancies and create a unified front against intellectual property theft. Treaties like the Agreement on Trade-Related Aspects of Intellectual Property Rights (TRIPS) provide a foundation, but enforcement remains inconsistent.
An effective deterrence strategy advocates for stronger bilateral and multilateral agreements that include clear provisions for addressing economic espionage. Joint efforts to track and prosecute offenders, share intelligence, and establish standardized IP protections are crucial steps toward reducing the global impact of this threat.
Organizational Resilllience: Insider Threat Programs
To counter insider threats, organizations must implement comprehensive risk management programs. Background checks, continuous monitoring of employee behavior, and strict access controls are essential components. Also effective are whistleblower protection programs that encourage employees to report suspicious activities without fear of retaliation.
Public-Private Partnerships: Leveraging Shared Expertise
Collaboration between the public and private sectors is vital to combat economic espionage. Governments can provide threat intelligence, while private organizations contribute technological expertise and on-the-ground insights. Initiatives like the FBI’s InfraGard program exemplify the potential of such partnerships to enhance national security and protect critical industries.
As the global economy becomes increasingly interconnected, the stakes of economic espionage continue to rise. By adopting a holistic approach that integrates technological, legal, and organizational strategies, society can safeguard its intellectual property and foster an environment of innovation and fair competition.

Best Practices: Renaissance Technologies
Renaissance Technologies, a legendary quantitative hedge fund, is a paragon of secrecy in the digital age. Founded by mathematician James Simons, the firm is renowned for its Millennium Fund, a private investment vehicle that has consistently outperformed the market. The fund leverages advanced mathematical models, big data, and machine learning to identify trading patterns invisible to human traders. Unlike traditional hedge funds, which rely on analysts and economic forecasts, Renaissance’s approach is purely algorithmic, making its proprietary systems its most guarded asset. This veil of secrecy, bolstered by nondisclosure agreements and an insular corporate culture, ensures the firm’s innovations remain out of competitors’ reach.
In the digital era, where data breaches and cyberattacks are rampant, Renaissance Technologies exemplifies how organizations can safeguard critical intellectual property. The firm’s Millennium Fund operates as a “black box,” revealing nothing about its strategies or operations. This secrecy mirrors the historical examples of hidden technologies, from the Wright brothers’ patents to DuPont’s titanium dioxide trade secrets. Just as these innovations required tight controls to prevent exploitation, Renaissance’s algorithms and data pipelines are fortified against external and internal threats. This extreme confidentiality not only preserves its competitive edge but also reflects the broader challenge of protecting digital assets in an interconnected world.
The story of Renaissance Technologies and its Millennium Fund ties directly to the themes of modern espionage and innovation security. In a landscape where digital espionage rivals physical theft, the firm’s ability to shield its methodologies underscores the necessity of robust defense mechanisms in protecting intellectual capital. From encrypted databases to legal safeguards, Renaissance’s approach is a case study in the art of hiding secrets in the digital age. It demonstrates that as technology evolves, so do the methods and stakes of protecting game-changing innovations, making vigilance and adaptability indispensable for organizations navigating the modern economy.

Policy and Legal Frameworks for Combating IP Theft
Efforts to combat intellectual property (IP) theft rely on a robust combination of domestic laws and international agreements. There are several key legal frameworks that have been instrumental in addressing economic espionage and trade secret theft.
The Economic Espionage Act (EEA) of 1996
The EEA was a groundbreaking piece of legislation that criminalized the theft of trade secrets. It established penalties for individuals and organizations involved in economic espionage, with harsher sentences for cases linked to foreign governments. The act also provided federal jurisdiction over trade secret theft, enabling more comprehensive investigations and prosecutions.
The Defend Trade Secrets Act (DTSA) of 2016
Building on the EEA, the DTSA created a federal civil cause of action for trade secret theft. This allowed companies to pursue lawsuits against perpetrators in federal court, streamlining the process for recovering damages and obtaining injunctions. The DTSA also introduced provisions for the seizure of stolen trade secrets to prevent their dissemination.
International Frameworks: The TRIPS Agreement
On the global stage, the Agreement on Trade-Related Aspects of Intellectual Property Rights (TRIPS) serves as a cornerstone for IP protection. Administered by the World Trade Organization, TRIPS sets minimum standards for IP rights enforcement among member countries. While it provides a framework for international cooperation, enforcement remains uneven, with some nations failing to fully comply with its provisions.

Challenges in a Globalized and Digital Economy
Despite these legal tools, significant challenges persist in combating IP theft:
- Jurisdictional Issues: Differences in legal standards and enforcement capabilities across countries complicate efforts to prosecute offenders and recover stolen assets.
- Rapid Technological Advancements: Emerging technologies, such as artificial intelligence, blockchain, and quantum computing (HNDL) create new vulnerabilities that existing laws may not adequately address.
- Attribution and Evidence Collection: Identifying perpetrators, particularly in cases involving cyber intrusions, is often difficult due to the use of anonymizing technologies and jurisdictional barriers.
- Economic Incentives for Non-Compliance: Some countries benefit economically from weak IP enforcement, making them reluctant to strengthen their legal frameworks.
Implications for Stakeholders
The lessons learned from these cases have far-reaching implications:
- For Businesses: Companies must prioritize investments in cybersecurity, employee training, and supply chain integrity to safeguard their intellectual property.
- For Governments: Enhanced international cooperation and stricter enforcement of IP laws are critical to addressing transnational threats.
- For Individuals: Awareness of the risks and consequences of engaging in economic espionage is essential for deterring potential offenders.
Combating economic espionage requires a proactive, multifaceted approach that addresses both systemic vulnerabilities and individual accountability.

Preparing for the Post-Quantum Era: Mitigating “Harvest Now, Decrypt Later” Attacks
As quantum computing advances, organizations must proactively defend against “harvest now, decrypt later” (HNDL) threats by transitioning to post-quantum cryptography (PQC). This requires adopting quantum-resistant encryption, updating public key infrastructure (PKI), and reinforcing data protection strategies to stay ahead of potential quantum-enabled decryption attacks.
Key Actions to Take Now
Adopt Post-Quantum Cryptography (PQC)
- Research and implement PQC algorithms best suited to your systems.
- Begin integrating quantum-resistant encryption in phases to ensure a smooth transition.
Strengthen Key Lengths
- Increase symmetric encryption key sizes (e.g., AES-256) to bolster security against brute-force attacks.
Implement Crypto-Agility
- Design systems that can easily switch to new cryptographic standards as quantum threats evolve.
Protect High-Value Data
- Prioritize securing sensitive information with layered security measures, including pre-shared keys where applicable.
Secure Communication Channels
- Explore quantum-resistant VPNs and other secure transmission methods to safeguard data in transit.
Educate and Prepare Stakeholders
- Raise awareness within your organization about quantum threats and the need for early PQC adoption.
Key Considerations
Quantum Computing is Advancing but Not Yet a Universal Threat
While large-scale quantum decryption isn’t possible today, attackers may store encrypted data to decrypt in the future.
No Single Fix—A Multi-Layered Approach is Essential
Effective defense requires a combination of PQC adoption, stronger key management, and secure communications.
Consult Security Experts
Engage cybersecurity professionals to evaluate your cryptographic posture and develop a tailored PQC migration strategy.
Taking these proactive steps now ensures your organization stays resilient against the inevitable rise of quantum computing threats.

Top Six Takeaways
Historical Roots of Economic Espionage. The practice of stealing secrets is not a modern phenomenon. Examples like Leonardo da Vinci’s coded notebooks underscore the age-old tension between innovation and espionage.
The Strategic Value of Intellectual Property. From Renaissance Italy to modern Silicon Valley, intellectual property has been a prime target for competitors and nations seeking strategic or economic advantage.
The Role of Technology in Economic Espionage. Advances in technology, from mechanical ciphers in da Vinci’s time to cyber espionage tools today, have continually shaped how secrets are stolen and protected.
State-Sponsored Espionage and Its Impact. Nations have long supported covert operations to access critical innovations. Modern examples include hacking campaigns targeting high-tech industries and defense contractors.
Private Sector Vulnerabilities. Companies, especially in cutting-edge fields like AI and biotechnology, face significant risks due to inadequate cybersecurity measures and insider threats.
Evolving Threats in the Digital Age. The rise of AI-driven tools and cyber-physical systems expands both the methods and targets for espionage, making robust security strategies more critical than ever.

“From da Vinci’s coded drawings to today’s encrypted data, the battle between innovators and those who seek to exploit their ideas will persist. In the post-quantum age, protecting secrets from harvest now, decrypt later (HNDL) means staying one step ahead with modern security measures and policies.”
Conclusion
The enduring relevance of protecting innovation is a lesson that resonates across centuries, from da Vinci’s intricate designs to the proprietary algorithms of today. The battle between those who create and those who seek to exploit their creations is a timeless struggle, yet one that has become increasingly complex in the modern age.
As threats evolve, so must our strategies to safeguard intellectual property. Robust policies, international collaboration, and modern security measures are not just optional but essential. In a world where the stakes continue to rise, the ability to protect innovation and hide secrets will define the winners and losers in the global race for economic and strategic dominance.
Additional Information
Sources, Acknowledgements and Image Credits
{1} Hiding Secrets: From Leonardo Da Vinci to Renaissance Technologies. Image Credits: PWK International Advisers. 07 FEB 2025
{2} Technological Surprise in Naval Warfare. Image Credit: Federal Bureau of Investigation (FBI), Undisclosed.
{3} Renaissance Technologies and the Millennium Fund. All registered trade marks and trade names are the property of the respective owners.
{4} This report mentions numerous innovation enterprises and their technological advances. All registered trade marks and trade names are the property of the respective owners.
About PWK International Advisers.
PWK International provides national security consulting and advisory services to clients including Hedge Funds, Financial Analysts, Investment Bankers, Entrepreneurs, Law Firms, Non-profits, Private Corporations, Technology Startups, Foreign Governments, Embassies & Defense Attaché’s, Humanitarian Aid organizations and more.
Services include telephone consultations, analytics & requirements, technology architectures, acquisition strategies, best practice blue prints and roadmaps, expert witness support, and more.
From cognitive partnerships, cyber security, data visualization and mission systems engineering, we bring insights from our direct experience with the U.S. Government and recommend bold plans that take calculated risks to deliver winning strategies in the national security and intelligence sector. PWK International – Your Mission, Assured.























































Pingback: Weaponizing Reality |
Pingback: Algorithmically Boosted Chaos |