
In the twenty-first century, the velocity of data has surpassed the velocity of data governance. Algorithms — once designed to optimize human systems — now amplify their chaos. They accelerate markets, radicalize communities, manipulate public opinion, and direct autonomous machines with unsettling precision.
This report will explore how algorithms, telemetry, machine vision and machine learning have transformed risk — creating a new ecosystem of instability where data and disruption move hand in hand.
The concept of Algorithmically Boosted Chaos describes a world in which every signal, click, and sensor reading contributes to a dynamic feedback loop of volatility, uncertainty, complexity, ambiguity . . . and worse.

Chief AI Officer (CAIO)
Chief Technology Officer (CTO)
Chief Innovation Officer (CINO)
Chief Digital Officer (CDO)
Chief Information Officer (CIO)
Chief Data Officer (CDO)
It’s not only about malicious code or cyber warfare; it’s about how the architecture of the digital age rewards speed and convenience, often at the expense of privacy, ethics, and security. In this environment, governments, corporations, and even individuals find themselves reacting to systems they can no longer fully understand, predict or even control.
This report examines how bad actor telemetry is impacting the birth of the age of AI and reshaping national security, financial markets, and social trust. It provides a framework for understanding how risk escalates across connected domains, and how risk accepted by one part of your enterprise is inherited by the rest.
Our report also delivers a blueprint, roadmap, and best practices guide for leaders seeking to manage complexity before complexity manages them.

TEN
EXAMPLES
OF BAD ACTOR
TELEMETRY
IN THE
AGE OF AI


Akira ransomware gang (ransomware-as-a-service, global) targeted over 250 organizations in 2023–2024, it used automated tools to select high-value victims (via scanning known vulnerabilities) and then encrypted data while exfiltrating it—and pressured victims via public leak sites. This algorithmic targeting and double extortion magnified damage and response times.
The Medusa ransomware group, active since 2021 and very prominent in 2023, used automation and network-of-access brokers to scale attacks across multiple sectors including healthcare and education, avoiding detection by using malicious drivers to disable endpoint protection tools. The speed and scope of these attacks were boosted by algorithms that optimized access, timing, and payload delivery.


In the Salt Typhoon cyberattack (late-2024, U.S.), a state-sponsored group breached multiple telecommunications providers using an algorithmic approach to map system weaknesses, then harvested metadata at scale—this combined espionage mode and ransomware-style pressure on infrastructure. The automated collection of data and use of zero-day vulnerabilities escalated the threat far beyond what a manual breach would have achieved.
The “ripple effect” in global supply chain disruptions shows how algorithmic demand forecasting and logistic automation create cascading failures: when a major hub is disrupted (e.g. by pandemic or conflict), automated systems shift demands, reroute orders, and overload backup suppliers, which themselves fail, creating regional and global shortages. Algorithms that try to adapt to one failure often amplify others


Recently discovered RansomAI proof-of-concept (2023) exemplifies malware using reinforcement learning to adjust its behavior (encryption speed, detection evasion) based on what the defending systems are doing—adapting its aggression to avoid heuristic detection. Because it learns in near-real-time, the chaotic impact increases as defenders’ systems lag
The Rorschach ransomware variant (2023) was identified for its rapid encryption speeds—encrypting tens of thousands of files in minutes—enabled by hybrid cryptography and partial file encryption. It demonstrates how speed and selective targeting driven by automated algorithms can overwhelm standard defenses.


In the global ransomware statistics up to mid-2024, LockBit / BlackCat / ALPHV and related variants rose in prominence, owing to affiliate networks, automatic leak sites that publish victim data, and dynamic negotiation scripts. These systems reward faster compromise and extortion, pushing victims and defenders into constantly escalating pressure.
The use of AI-powered ransomware “PromptLock” (recent discovery) shows how adversaries are starting to embed large language model components to fragment detection—generating unique scripts dynamically to evade heuristic or signature-based detection. The non-deterministic behavior adds unpredictability to what defenders must guard against.


The Scattered Spider / ALPHV-BlackCat breach of MGM Resorts and Caesars in 2023 used automated reconnaissance (via social engineering, identity data on LinkedIn), privilege escalation tools, and automated scripts to map and exfiltrate data. Then ransomware deployment and systems shutdowns were orchestrated swiftly, maximizing impact and minimizing response time.
The rising number of healthcare sector ransomware attacks (2024–2025) demonstrates an algorithmic pattern: threat actors use data-leak timelines, automated victim selection (e.g. targeting facilities with previous vulnerabilities), and public shaming / countdown threats to force payment. The scale—hundreds of facilities, massive data compromised—shows how algorithmic methods convert what were once sporadic events into systemic crises.

NOTICE: Our unbiased analysis includes mention of specific ransomware as a service providers and innovators. All registered trade marks and trade names are the property of the respective owners.

The Blueprint: Mapping the Architecture of Chaos
At its core, algorithmic chaos is about speed and amplification. Algorithms, whether embedded in financial markets, social media platforms, or autonomous systems, are designed to accelerate decision-making and optimize outcomes. Yet in the wrong hands—or under the pressure of global crises—these same systems become accelerants of instability.
Disinformation and Social Media: A false story used to take days or weeks to spread; now it can go viral globally within minutes. Social media algorithms are optimized for engagement, not truth, and bad actors exploit this to amplify divisions, manipulate elections, and stoke and even organize for violence.
Cyberattacks and Ransomware: Digital crime has shifted from isolated breaches to systemic crises. Ransomware spreads through interconnected systems, where one vulnerability can cascade into hospital networks, municipal governments, and supply chains simultaneously. Algorithms used by attackers automate the targeting, propagation, and monetization of these attacks.
Supply Chain Shocks: Modern supply chains are algorithmically managed, balancing inventories across global networks. But disruptions—whether due to pandemics, war, or sanctions—are amplified as algorithms react in real time, sometimes deepening shortages or price volatility.
From Lone Wolf to Network Effect. A decade ago, a single terrorist or criminal might have inflicted local damage. Today, that same act, livestreamed on social media, algorithmically promoted, and echoed by extremist networks, can inspire copycats globally. A lone wolf becomes a node in a global system of chaos.
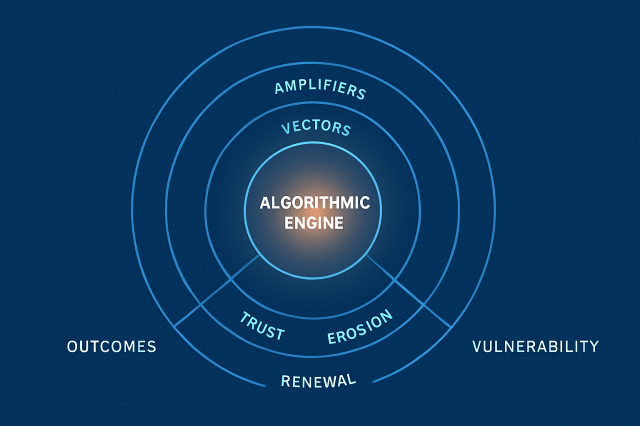
Algorithmically boosted chaos represents a shift in both scale and speed. Instead of one-off risks, we face ecosystems of disruption where feedback loops spiral out of control.
SOURCE | PWK International
Amplifiers turn data into instability. Social media algorithms accelerate outrage, while dark web platforms provide anonymity for illicit coordination. State-backed influence operations weaponize these same systems to shape narratives and distort perception. In this ecosystem, the algorithm doesn’t need to “choose sides” — it merely optimizes for engagement, not truth. The result is a structural amplification of chaos.
Vectors of disruption emerge through biological, environmental, criminal, and geopolitical channels. Pandemics spread misinformation as quickly as infection. Climate shocks trigger migration and scarcity. Ransomware cripples hospitals and pipelines. Election tampering and proxy wars erode trust in global governance. These are not isolated events but interconnected signals in a digital storm at the birth of the age of AI. Understanding this web of escalation is the foundation of the blueprint for algorithmic risk.


If you like this report . . then you may also enjoy . . .
WEAPONIZING REALITY

Bad Actor Telemetry
The concept of bad actor telemetry reframes how we understand adversaries in the modern era. Every bad actor leaves a digital footprint—financial transactions, social media activity, communications metadata, and even movement through physical and cyber terrain. Tracking, analyzing, and interpreting this telemetry has become central to security operations.
Telemetry in Practice: Blockchain analytics firms can trace illicit cryptocurrency flows used by ransomware groups. Social listening platforms can detect extremist chatter before it materializes into violence. Intelligence agencies use metadata patterns to identify networks of smugglers, traffickers, and spies.
The Dual-Use Problem: Telemetry is not a one-way advantage. Just as governments and corporations track adversaries, bad actors are learning to exploit telemetry themselves. Cybercriminals analyze security firm behavior, adapt ransomware strains algorithmically, and exploit algorithmic blind spots in detection systems. Nation-states conduct telemetry warfare, flooding digital channels with false signals to obscure their true operations.
Dark Web Laundering vs. Blockchain Analytics. Crypto laundering networks attempt to anonymize transactions through mixers and decentralized finance platforms. Yet blockchain analytics firms, leveraging advanced algorithms, often unmask these flows and provide actionable intelligence. The result is an ongoing cat-and-mouse game of telemetry manipulation.
Bad actor telemetry is thus the new battlespace. Success in modern security will depend not only on intercepting signals but on understanding the algorithms that generate, interpret, and distort those signals, particularly as agentic AI accelerates.

The Roadmap: From Detection to Renewal
The roadmap to resilience follows five phases — detection, containment, resilience building, counter-algorithms, and renewal. It begins with detection, the capacity to see anomalies before they cascade. Governments and corporations must establish real-time telemetry awareness — not just network monitoring, but behavioral analytics across systems that indicate when chaos is accelerating.
Containment requires segmentation. Once a threat is detected, isolation becomes the priority. Redundant networks, sandboxed communications, and instant data lockdowns can prevent one failure from triggering another. The third phase, resilience building, emphasizes redundancy as design: diversified supply chains, distributed energy systems, and leadership training in complexity thinking. Resilience is not a contingency plan; it is a standing posture.

Counter-algorithms mark a proactive shift. Just as adversaries use machine learning to predict weakness, defenders must deploy predictive models to simulate potential points of failure. Red-teaming with adversarial AI — simulating algorithmic manipulation or misinformation campaigns — allows institutions to preempt rather than react. Finally, renewal closes the loop. After each disruption, rebuilding trust, transparency, and institutional credibility becomes the ultimate act of strategic restoration. Renewal is how societies learn faster than the systems that challenge them.
Best Practices: Guidelines for the Algorithmic Age
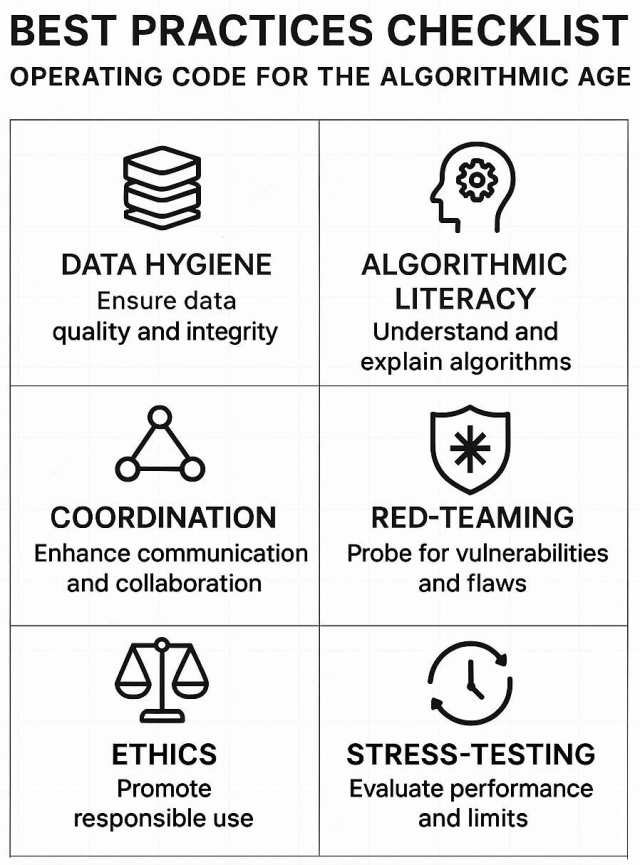
Managing algorithmic risk requires a disciplined set of principles. The first is data hygiene — encrypting, anonymizing, and segmenting critical information. Every unprotected dataset becomes a potential weapon in the wrong hands. The second is algorithmic literacy. Leaders must understand not only what algorithms do, but how they think. Hallucinations, bias, virality, and feedback loops are not just bugs; they are structural properties that can destabilize entire systems if misunderstood.
The third best practice is scenario red-teaming — wargaming complex, algorithm-driven crises such as flash crashes, misinformation floods, or cross-domain cyberattacks. These simulations convert theoretical vulnerabilities into operational awareness. Fourth, cross-sector coordination becomes essential. No agency, corporation, or nation can manage algorithmic risk in isolation. Shared intelligence networks and joint exercises between public and private sectors create the connective tissue of resilience.
SOURCE: PWK International
In this new era of exponential progress, efficiency and unpredictability coexist—producing both unprecedented capability and systemic chaos.
We recommend our clients subscribe to a six (6) part operating code that offers enterprises of all sizes a risk framework for controlling and mitigating algorithmic chaos in the age of AI.
Finally, ethical guardrails and continuous stress-testing are the twin anchors of digital governance. Innovation without ethics amplifies instability, while static systems invite surprise. Embedding ethical oversight and routine vulnerability testing ensures that resilience evolves in step with technology. The organizations that thrive in this era will treat resilience as a living system — constantly measured, questioned, and improved.

Top Six Takeaways
- Algorithms amplify instability. They are not neutral tools but accelerants of feedback loops that can turn localized disruptions into systemic crises.
- Telemetry is the new battlespace. Every digital signal — from consumer data to satellite feeds — can be exploited to predict, influence, or destabilize.
- Detection must precede containment. The faster anomalies are recognized, the smaller their impact on the system.
- Counter-algorithms are essential. Defending against automated chaos requires equally intelligent systems capable of forecasting manipulation.
- Resilience is designed, not declared. It depends on redundancy, coordination, and leadership capable of navigating complexity.
- Ethics is strategy. Responsible AI development and transparent governance are not moral luxuries — they are national security imperatives.

Conclusion: Harnessing Chaos for Strategic Coherence
Algorithmically boosted chaos is not a future scenario — it is the operating condition of the present. The same algorithms that optimize trade routes, financial systems, and communications also carry within them the seeds of accelerated disorder. The challenge for modern leaders is not to halt technological evolution, but to embed foresight into its architecture.
This report demonstrates that chaos, when understood, can be managed — and when mapped, can even be turned to advantage. By aligning technology with governance, resilience with design, and ethics with innovation, nations and organizations can convert algorithmic volatility into adaptive strength. The goal is not to return to control, but to achieve coherence: a steady hand amid accelerating complexity.
In a world governed by data, those who understand how chaos is algorithmically boosted — and how to enable an agile and resilient response will be the winners in a world filled with increasing volatility, uncertainty, complexity and ambiguity.

Acknowledgements and Image Credits
{1} Algorithmically Boosted Chaos | Bad Actor Telemetry in the Age of AI. In the twenty-first century, the velocity of data has surpassed the velocity of governance. Algorithms — once designed to optimize human systems — now amplify their chaos. Credit: PWK International. 10/13/2025
{2} Salt Typhoon Photo-Illustration: Credit: Darrell Jackson/Getty Images
{3} Ransomware Image: Credit: Shutterstock
{4} Algorithmically boosted chaos thus represents a shift in both scale and speed. Instead of one-off risks, we face ecosystems of disruption where feedback loops spiral out of control faster than traditional defenses can react. Image Credit: PWK International 10/10/2025
{5} The concept of bad actor telemetry reframes how we understand adversaries in the modern era. Every bad actor leaves a digital footprint—financial transactions, social media activity, communications metadata, and even movement through physical and cyber terrain. Image Credit: PWK International 10/10/2025
{6} The Roadmap: From Detection to Renewal. Chart Credit: PWK International 10/11/2025
{7} Best Practices | We recommend our clients subscribe to a six (6) part operating code that offers enterprises of all sizes a risk framework for controlling and mitigating algorithmic chaos in the age of AI. Credit: PWK International. 10/11/2025
{8} Algorithmically boosted chaos is not a future scenario — it is the operating condition of the present. The same algorithms that optimize trade routes, financial systems, and communications also carry within them the seeds of accelerated disorder. Credit: PWK International. 10/09/2025
{7} NOTICE: Our unbiased analysis includes mention of specific ransomware as a service providers and innovators. All registered trade marks and trade names are the property of the respective owners.
Additional Information:


About PWK International
PWK International is a strategic research and consulting firm exploring how technology, innovation, and government intersect to shape the modern world. We deliver deep analysis on emerging systems—from artificial intelligence and advanced defense programs to procurement reform and digital governance—to help clients anticipate disruption before it happens. This report continues that mission by decoding the algorithmic forces driving new forms of volatility and influence across global systems.
Our team serves technology firms, defense contractors, investors, and policy professionals navigating complex innovation landscapes. We help organizations translate abstract trends—automation, data fusion, algorithmic decision cycles—into concrete strategies for operational advantage and risk mitigation. Whether you build products, manage programs, or shape public policy, our insights help you align technology decisions with strategic outcomes.
At PWK International, we believe foresight is the new competitive edge, and have a reputation for delivering value with technology, expertise and integrity. Each report we publish provides a blueprint for understanding the next era of government, business, and power. Algorithmically Boosted Chaos exemplifies that approach—turning the world’s emerging disorder and algorithmically boosted chaos into a roadmap for better governance, smarter investment, and resilient innovation.





















































Pingback: China in New Mexico |